(UPDATE: Sevan Janiyan pointed out the Sun 2 was not a SPARC system)
Yesterday, Alec Muffet posted a few tweets regarding the Sun SPARC 2 bootloader’s DES routines.
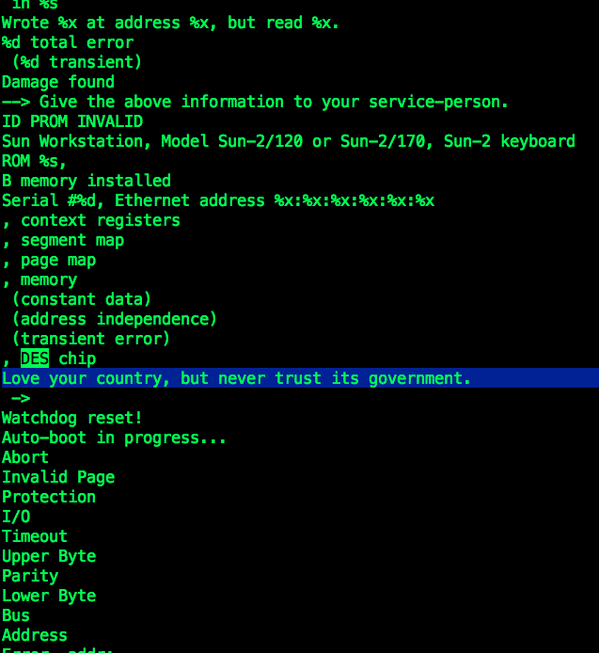
Alec figured that message was never supposed to be seen and suggested it was a kind of silent protest of someone in Sun against the US Government. I replied, saying I was pretty sure such a message anywhere in the Sun bootprom code must have originated by John Gilmore. So I asked John, and he did not disappoint. This is what I wrote me back:
> That must have been you? :)
Yes. Vinod Khosla, first President of Sun, came to me at one point
and said to put something hidden, triggered in an unexpected way, into
the ROM Monitor, so that if somebody cloned the Sun Workstation
(violating our software’s copyright), we could do that unexpected thing
to the competitor’s demo workstation at a trade show and thereby prove
that they had cloned it.The ROM Monitor command that printed “Love your country, but never
trust its government.” was “k2” followed by control-B and RETURN. (To
get to the ROM Monitor from the running Unix display, you had to hold
down the L1 key and hit “A” then release both; the monitor had special
code looking for that key sequence.) I had found that saying years
before on a hand-painted sign tacked up on a pole or tree in central
Pennsylvania, wrote it into one of my notebooks at the time, and
plucked it out as the hidden thing after Vinod asked. In the source
code it was obscured as a set of hex numbers, but in the binary it was
visible. (I didn’t bother to XOR it with something to make it more
hidden.)The circumstance Vinod was concerned about never did come about;
nobody stole the Sun boot roms. Early 680x0s didn’t come with a
standard MMU, so everybody who wanted virtual memory had to invent
their own, and our roms were very tied to our custom static-ram based
zero-wait-state MMU, which was also patented. A few companies
licensed the board design from us, like Imagen for a laser printer
controller, but they had a license to use the ROMs.The DES chip slot was intended to speed up DES for high security
networking applications, and we did get it working. I think Bill Joy
was the one who made it a part of the architecture, all the way
through the Sun-3, thinking that we’d use it as part of securing the
network file system. But the chip was expensive and
export-controlled, and our software never really used it (NFS ran in
plaintext and used the sender’s IP address for authentication!). So
it didn’t get stuffed on the production boards, and eventually they
stopped stuffing the support chips too. Tom Lyon wrote a nice device
driver for it, and a “des” user command that would use the chip for
file encryption if it existed (or fall back to software).
In one 68010 based model we also put in a slot for an Intel floating
point chip — I think the one that came with the 80286. We got it
working (I did the initial debugging) and fed it commands and
arguments via manual peek/poke in software. Doing that was somewhat
faster than the software floating point that we were otherwise using,
despite the overhead. But as I recall, Intel wouldn’t sell us the
chips in volume, because they didn’t want to make the 68000 more
competitive against their own x86 chips. So we had to wait til the
68020/68881 came out (Sun-3 era) before we had fast floating point.It’s nice that Matt Fredette made a Sun-2 emulator. I may have
images of old SunOS release tapes that might work in it. And I have a
Sun “FE Handbook” for the field engineers, that has a lot of the
details about what chips go where, what the jumpers on each board
mean, what the memory map of each board looks like, and etc.You can forward this info on to whoever…
John

John doesn’t explain why the message is seen, in spite of the easter egg command sequence not being given.
He does. He writes which key combination to press to get the message displayed. He also explained it was to check if someone stole their code if they had access to a keyboard – like in a trade booth
Yes, I got that part; the question is why it appeared in the boot log which is seen. Presumably, the operator didn’t type those keystrokes.
Note that the message appears just after the “DES Chip” line. And in the article, John writes about the DES chip and a “des” command, and there is a reference to some earlier tweets about the DES routines. There is some connection between the DES stuff and this easter egg.
OK, mystery solved, I think. The tweets appear to be about looking for strings inside that firmware with the strings command. I think what we are seeing in the image above is a snapshot of a part of the output of “strings file.bin” where file.bin is the firmware image. I think there is no connection, accidental or otherwise, between the DES chip support and the message. Just the string is close to some DES-related strings.
It was not visible in the source code, because then bytes are represented in hex; but it is plainly visible when you use strings on the binary.
You’ll note that the image has percent-escaped printf formatting characters. This would be the output of the ‘strings’ command on the binary.
John mentions not XORing the text in the binary to hide it, therefore it was plainly visible among the set of other strings.
> “It’s nice that Matt Fredette made a Sun-2 emulator.”
I also made one, more than twenty years ago, to a certain level of completion. I was taking a kernel hacking university course, and the work involved running Douglas Comer’s XINU on Sun 2’s and 3’s.
We didn’t have enough machines for everyone to use at the same time, so whipped up a 68010 emulator, with handling for some of the hardware.