UPDATE: Statistics updated to include 2017
Yesterday, openswan released version 2.6.40 to address CVE-2013-6466. You might be confused by its changelog (not the non-updated CHANGES) crediting me for the vast majority of code changes. . Basically all changes are pulled from the libreswan repository and are backports to openswan. The exception is their version of a patch for CVE-2013-6466. Libreswan’s fix is not a band-aid but an updated state machine. The backported libreswan fix is what is going into the updated openswan packages for RHEL5 and RHEL6 and are available at libreswan.org/security/openswan/CVE-2013-6466. RHEL7 will contain libreswan.
Basically, yesterday’s openswan 2.6.40 release brings it up to the initial libreswan-3.0 release of two years ago, plus the two CVE issues. Except that it crashes KLIPS and backported a libreswan commit that broke all non-XAUTH IPsec connections.

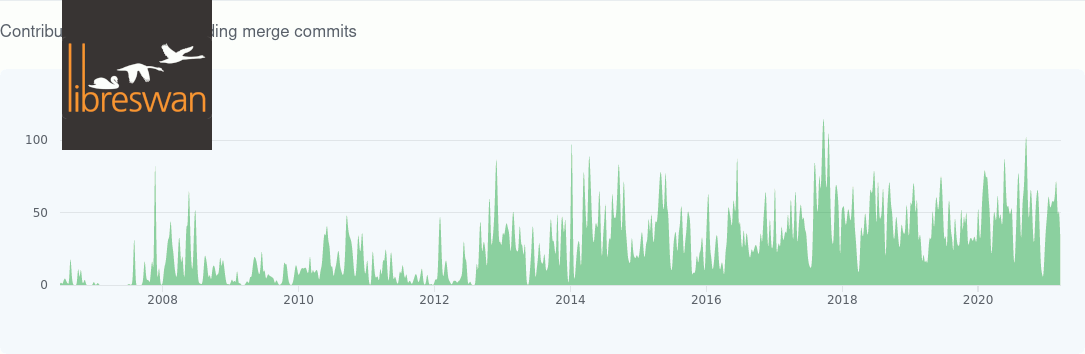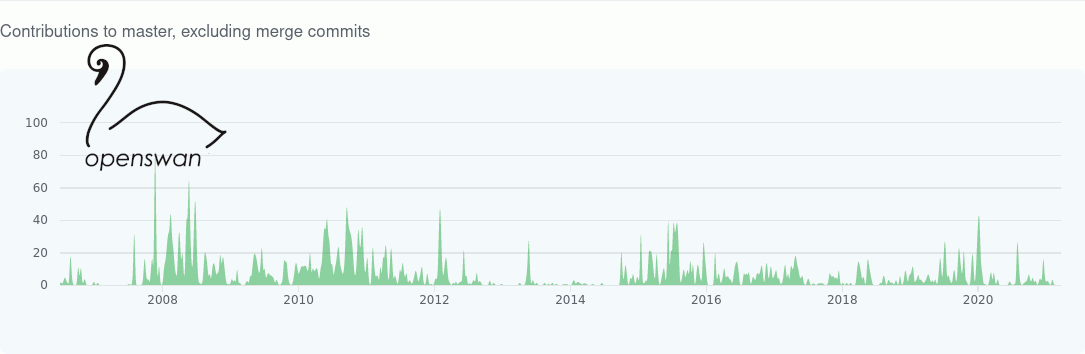
And this is why I switched to Libreswan.
Pingback: IPsec/L2TP VPN Auto Setup for Ubuntu with Libreswan « Worldpillar
hello sir
Sir let me know what is the basic diffrence between openswan and libreswan.
libreswan is the continuation of openswan. Openswan has not seen any meaningful development in the last few years. See swan development statistics
What about strongswan? Isn’t it the de-factor standard in distros? Any thoughts of that?
I was recently thinking about switching to libreswan from strongswan, but couldn’t find a real comparison. Looks like strongswan has more features and a newer codebase, while libreswan depends on a rock solid core, but that’s subjective…
strongswan is a good solution too. There are various pro’s and cons for libreswan vs strongswan.